The hidden risks with Typosquatting
Typosquatting related to package management poses hidden risks to software developers.
Attackers can create package names with typos that closely resemble legitimate packages and upload them to public repositories, which can go undetected.
If developers or CI/CD systems mistakenly install these packages, they can introduce malicious code into their software application and compromise its security.
The consequences of such an attack can range from data breaches to unauthorized access to sensitive information, which can have severe consequences for both individuals and organizations.
The hidden nature of typosquatting attacks often makes it difficult for companies to detect and prevent them. As such, it is crucial for developers and users to be vigilant when installing packages, avoid using unverified or unofficial sources, and carefully verify package names and sources.
Developers should be very restrictive, especially when installing newly published packages, as attackers deploy new versions as they often only go undetected for a few hours or days.
Malware is often installed through Typosquatting and it’s important to protect the developer workstations and other system environments from getting the malicious packages installed.
An accidental installation may lead to big problems: Malware can take many forms, including viruses, trojans, and ransomware. Once installed it can cause a range of problems, including stealing sensitive data, disrupting system operations, and even locking users out of their systems.
Typosquatting is an effective method of distributing malware because users may not realize they have downloaded and installed a malicious package, especially if they are in a hurry or not paying close attention.

The impact of Typosquatting
Understanding the impact of typosquatting is important for companies to protect themselves from potential financial, legal, and reputational consequences.
Typosquatting attacks have become a growing threat to companies that rely on packages from popular package managers such as npm, PyPi, NuGet, and Maven. The intent with these attacks are almost always tricking developers into installing malware-infected packages or stealing sensitive information.
It is important to understand the scope of the problem. In recent years, there have been several high-profile typosquatting attacks on popular package managers, and thousands of malware packages are published to their public package repositories. Headlines like 500 malware packages published to PyPi or 1000 npm packages targeting Azure users are unfortunately not uncommon.
Attackers are often targeting packages that are popular in order to get as many downloads as possible. Some malicious packages only get a few hundred downloads before they are removed, but often they get many more. Downloading one bad package can have devastating consequences.
In 2022, the PyPi package named pymafka (very similar to pykafka which has 4 million+ downloads) was discovered to contain a backdoor on Windows, Linux and MacOS that allowed attackers to cause significant damage on infected systems.
In 2018, the npm package eslint-scope, designed to steal crypto- wallets, was downloaded 1000+ times before it was removed from the registry. This means not much has changed, other than that the attacks are more sophisticated today.
The sophistication level of the typosquatting attacks varies of course. Some attackers essentially create a wrapper around the legit package, and only execute the malicious code on certain events. Applications continue to work as expected, and with obfuscated code, these attacks can be very difficult to detect.
These attacks can have serious consequences for targeted companies. Malicious packages can introduce vulnerabilities into a company’s software supply chain, which can be exploited by attackers to gain access to sensitive data or disrupt operations. In addition, companies may face legal and reputational consequences if their software is found to contain malware-infected packages.
The one keystroke mistake that could cost a developer everything
Reavt is a live example of users downloading the wrong package
If you’re a developer, you know that installing the wrong package can lead to all sorts of issues. But what if the package you thought you were installing wasn’t actually the package you received? That’s the danger of Typosquatting, and it’s more common than you might think.
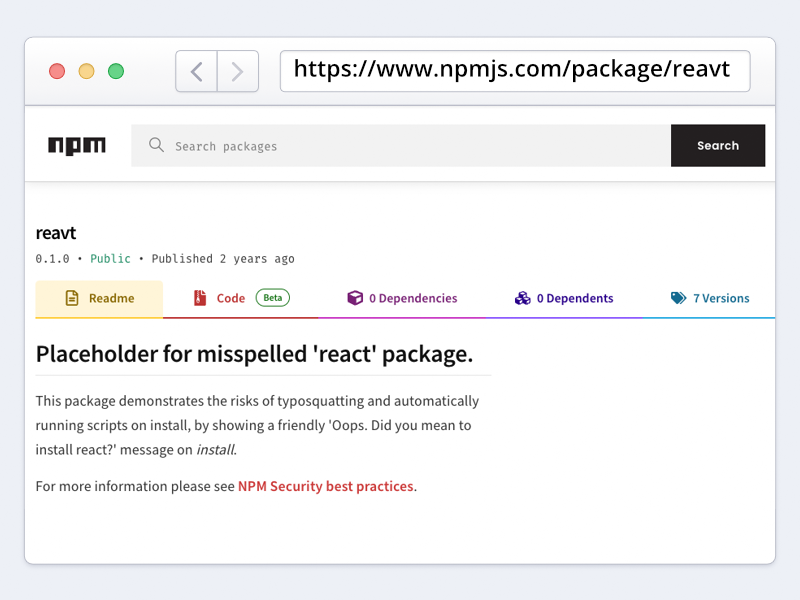
To demonstrate the dangers of Typosquatting Bytesafe has published the package called reavt to the public npm registry. It’s spelled almost identical to the popular react package.
It’s easy to see how a developer in a rush might make this simple mistake, and that’s exactly what attackers are hoping for.
Installing reavt only gives a warning to the developer.
$ npm install reavt
npm ERR! code 1
npm ERR! path /code/myproject/node_modules/reavt
npm ERR! "Oops. Did you mean to install 'react'?"
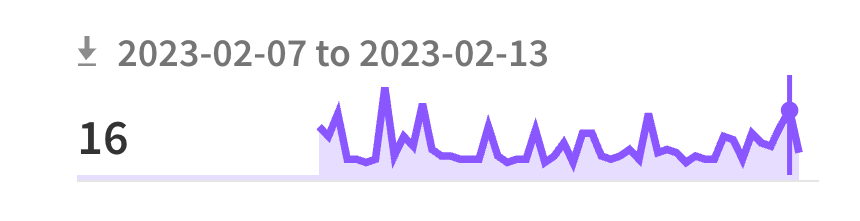
The fact that the reavt package is downloaded multiple times every day shows that many developers make simple typos when installing packages. The proximity of the v and c keys on the keyboard may be one reason for the confusion.
What’s the worst that could happen if you accidentally installed a malicious package? The consequences could be devastating, from data theft to system takeover. Even if a developer quickly realizes the mistake and installs the correct package, it might already be too late.
Don’t let a simple typo cost you everything - read on to learn how to protect yourself and your system from potential threats.