Generate SBOMs and operationalize compliance
Software Composition Analysis
SBOM Observer unifies SBOM creation, validation, and analysis so security, compliance, and engineering teams can collaborate.
Use the open source Observer CLI to build SBOMs from source, images, or environments, then upload them to SBOM Observer to monitor risk, enforce policy, and deliver regulator-ready evidence.

Why SBOM-centric workflows matter
The problems you are facing
SBOM Observer + Observer CLI
Software Composition Analysis
Use the open source Observer CLI to generate SBOMs from builds, repositories, or container images, then analyze them in SBOM Observer to enforce policy and share proof.

Generate SBOMs anywhere
Observer CLI is fast, CI/CD-ready, and supports CycloneDX and SPDX. Create SBOMs from source directories, containers, Kubernetes clusters, or build pipelines, enforce policy gates, and upload directly to SBOM Observer.
- Supports CycloneDX / SPDX
- Fail builds automatically when policies are violated
- Analyze and automate from CI/CD
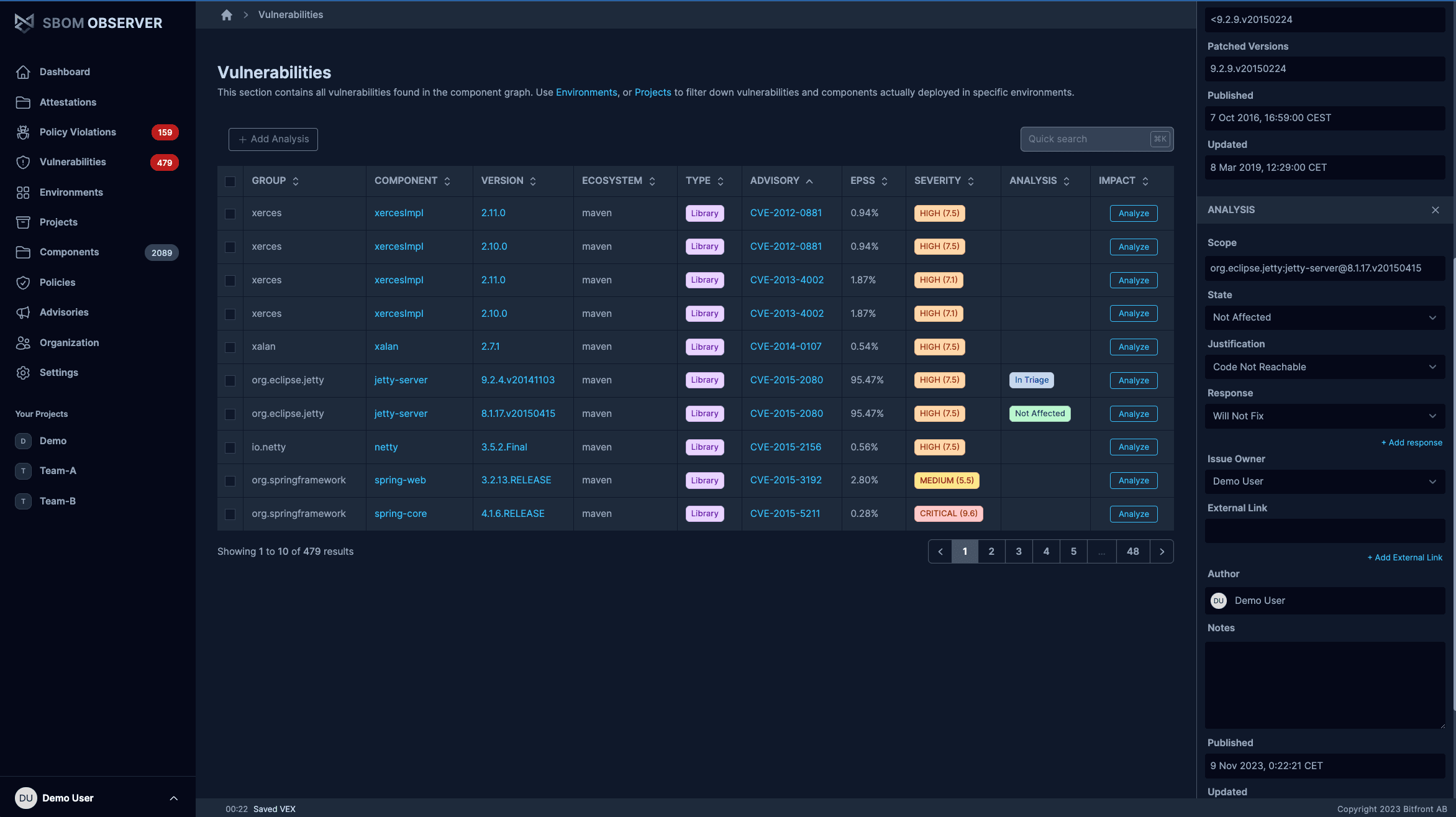
Contextual vulnerability intelligence
Move beyond raw CVE lists to understand real impact. Get actionable context with affected components and downstream impact analysis, and prioritize fixes based on business needs.
- Monitor vulnerabilities across all tracked components
- Visualize impact analysis
- Prioritize with business and exploit context
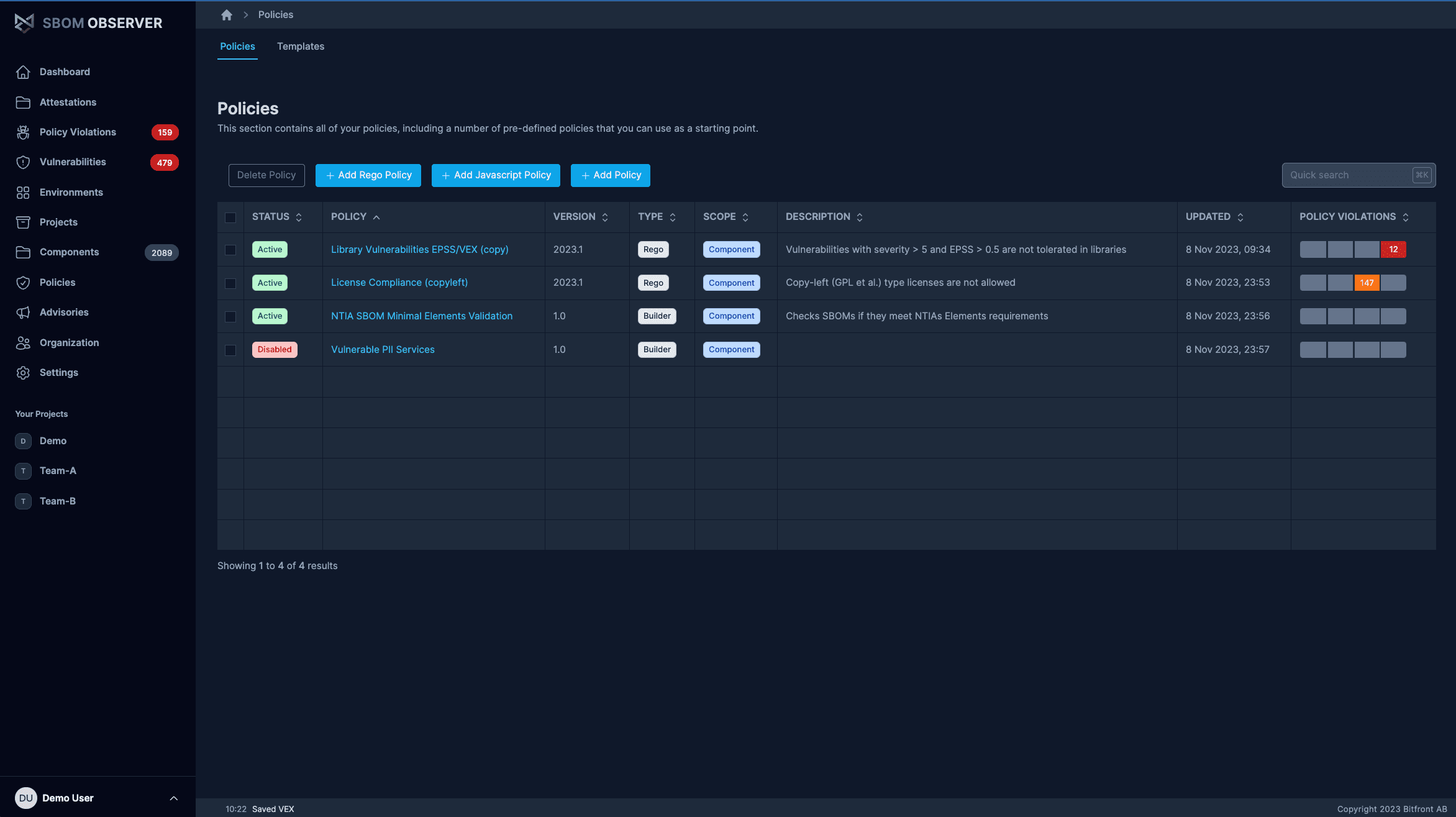
Policy engine & automated enforcement
Define policies and apply automated checks across your supply chain. Flag non-compliant components and surface violations early in development workflows.
- Align controls with DORA, CRA, NIS2, or customer requirements
- Validate every release in CI/CD and fail builds on violations
- Create and maintain security and compliance policies centrally
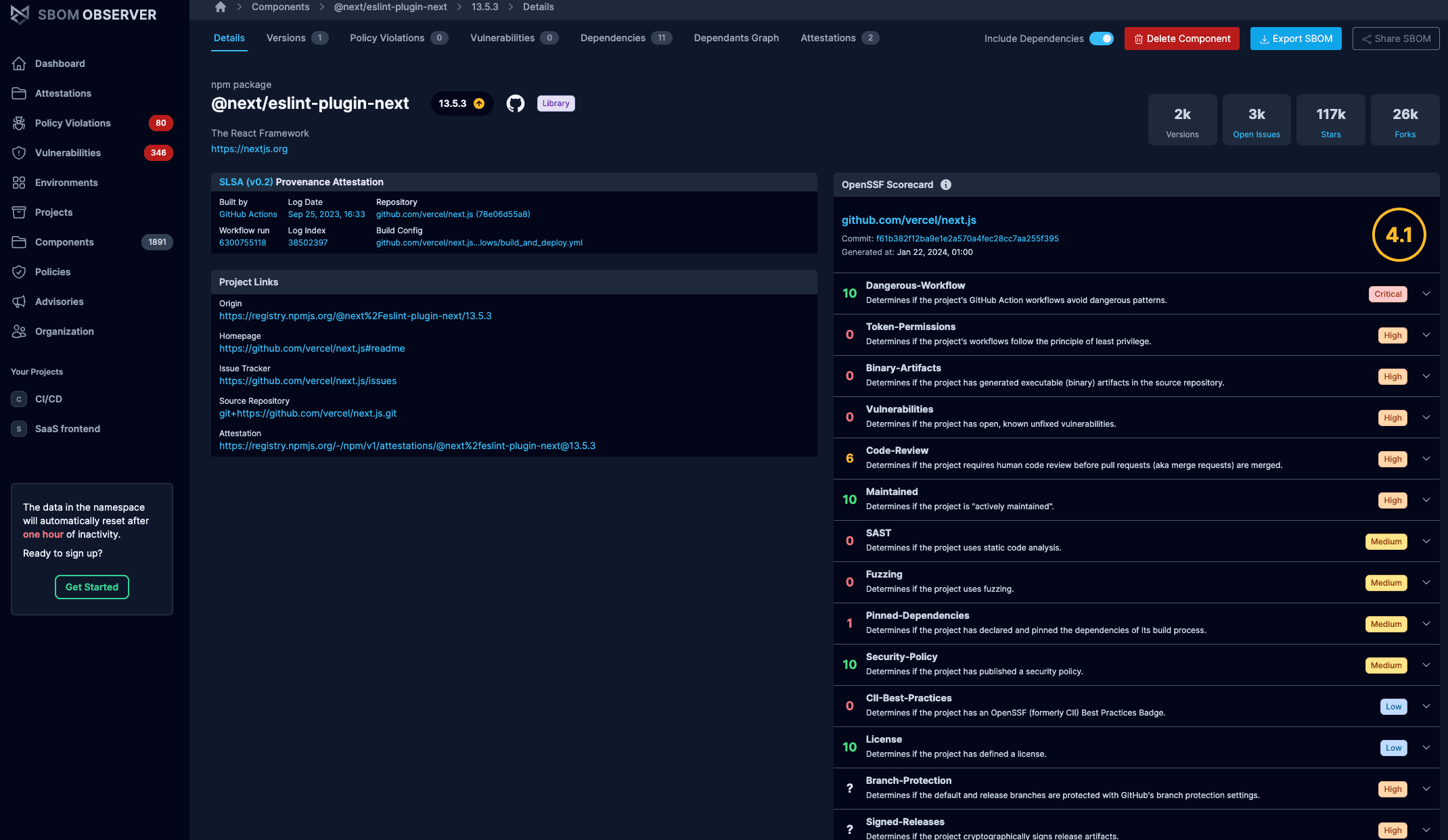
Risk analytics & reporting
Visualize and quantify supply chain risk exposure. Explore dashboards that surface vulnerabilities and impacted components for specific applications and releases.
- Dashboard views highlight vulnerabilities per application
- Enriched data exposes SLSA provenance alongside SBOM insights
- OpenSSF Scorecard signals highlight dependency health


