
A critical remote code execution (RCE) vulnerability was identified March 30th, 2022 for the Spring Framework. Spring core, used by millions of systems to develop Java web applications quickly, is one of the Java world’s most popular open source Java frameworks. The RCE vulnerability, if successfully exploited could potentially allow an attacker to take control of a vulnerable system.
The vulnerability stirred some initial confusion regarding if the exploit was a new or old 0-day or even reachable. Since then the Spring team has confirmed the vulnerability, and the vulnerability has been assigned CVE-2022-22965.
The timing brings attention back to the recent Log4j incident that even after several months has organizations around the world working to patch vulnerable applications.
The Spring vulnerability, dubbed Spring4shell or SpringShell, and the ongoing work to patch Log4j highlights the importance of a secure software supply chain for the Java ecosystem, where organizations can know and trust the open source dependencies their applications depend on.
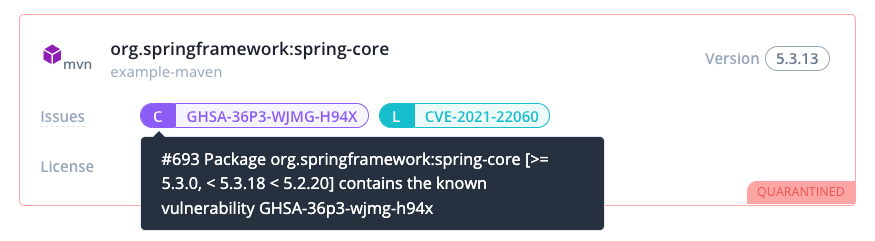
Determining the impact of CVE-2022-22965
The Spring team has released the following requirements to identify affected applications:
- JDK 9 or higher
- Apache Tomcat as the Servlet container.
- Packaged as a traditional WAR (in contrast to a Spring Boot executable jar).
spring-webmvcorspring-webfluxdependency.- Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and older versions.
However, the nature of the vulnerability is general and there may still be other ways to exploit the vulnerability.

Upgrade to a patched version to remediate
The recommended path by the Spring team to remediate the vulnerability is to upgrade to a safe patch version.
Spring Framework: 5.3.18 and 5.2.20 that contain fixes have been released.Spring Boot: 2.6.6 and 2.5.12 that depend on Spring Framework 5.3.18 have been released.
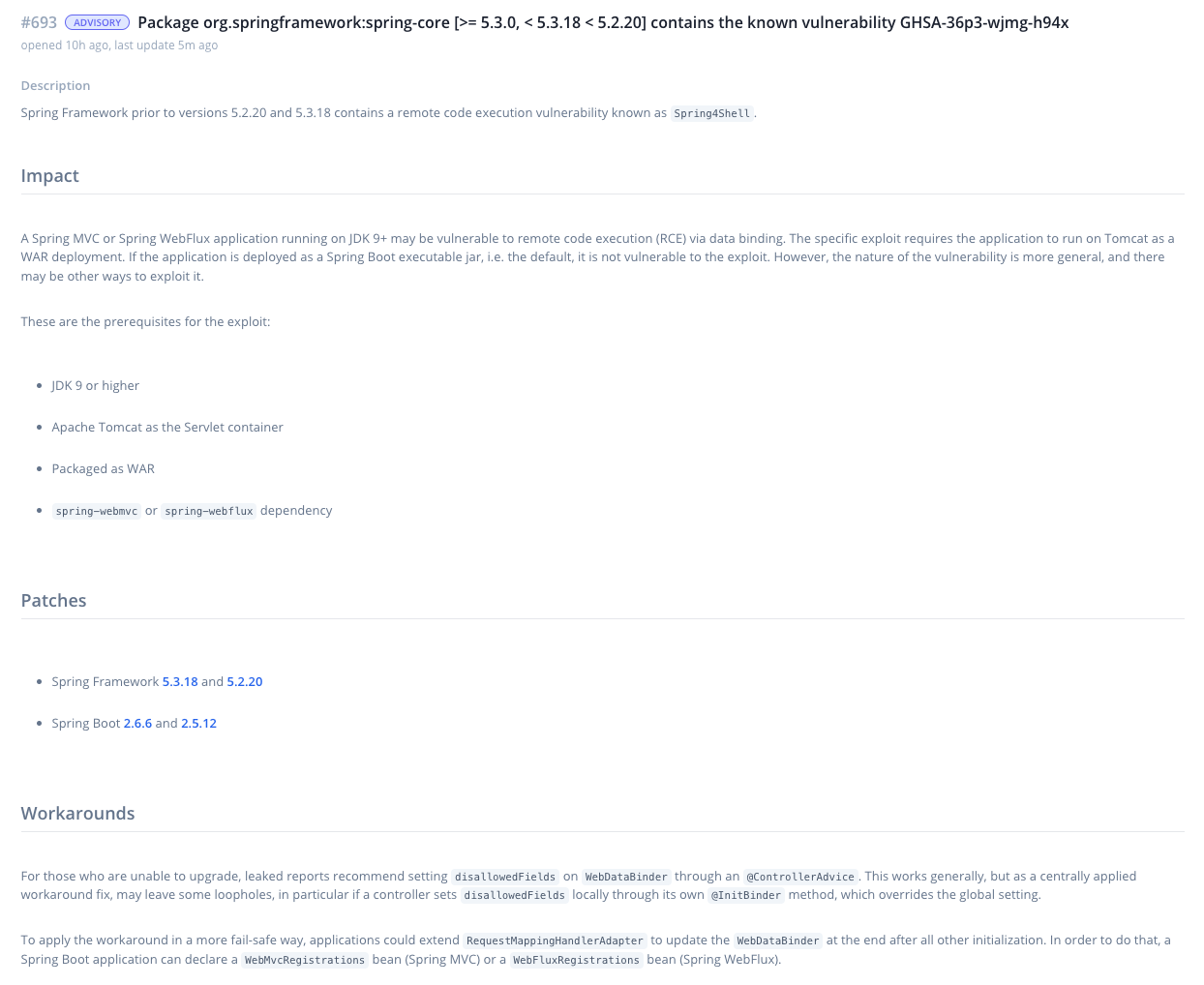
For more details and possible workarounds, see the advisory in Bytesafe or view it on GitHub: CVE-2022-22965.
How to identify if you’re using the Spring framework in your organization?
Knowing where a package is used in distributed environments, across teams and developers can be the biggest challenge when dealing with security incidents.
Fortunately Bytesafe keeps track of your package dependencies - allowing you to remediate faster and see the overall risk.
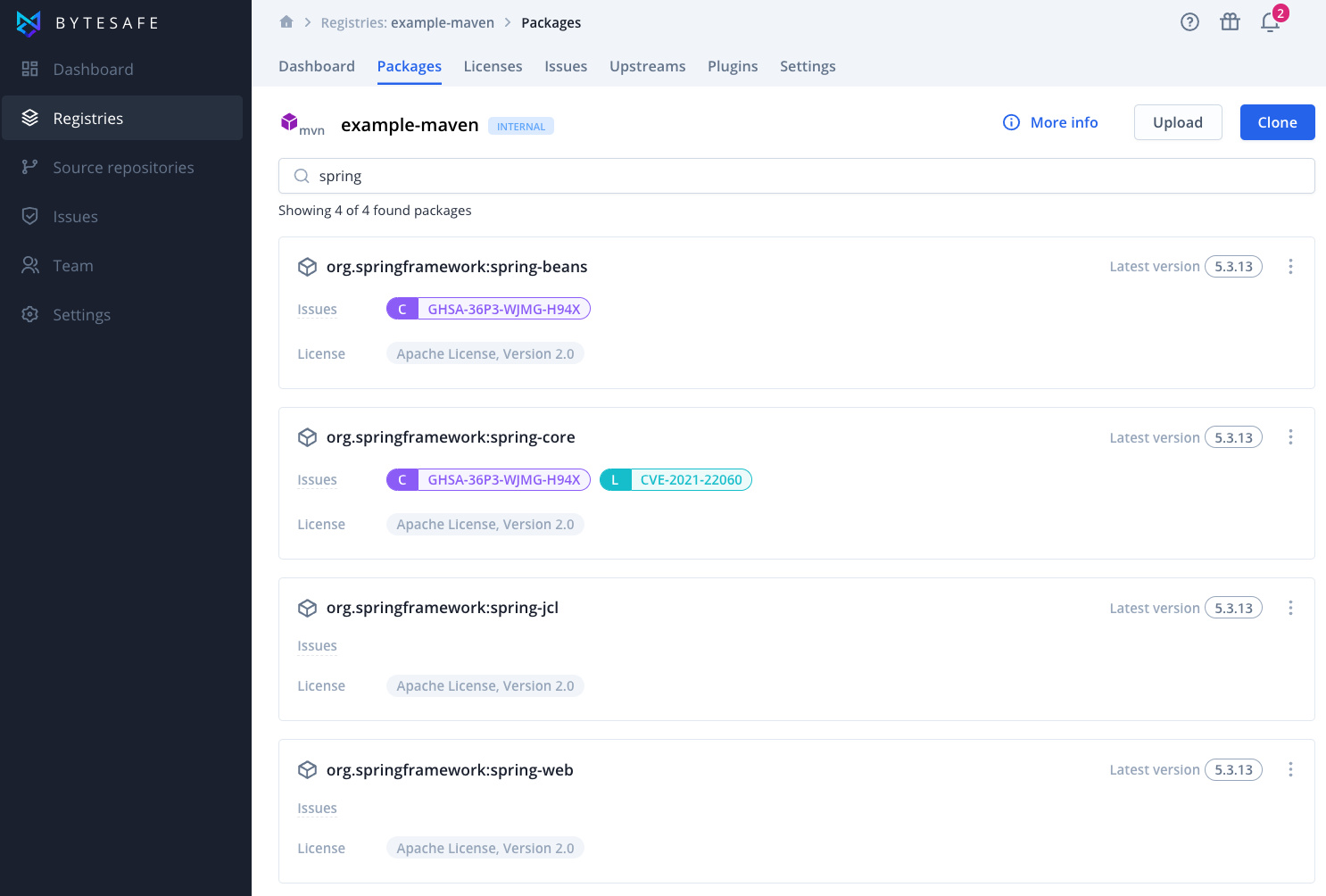
Advanced package search in registries
Packages stored in Bytesafe are easily identified by searching registries.
Simply enter a search term (e.g. spring) to identify any matching packages and click the package card to view available versions.
Automatic issue tracking and quarantine
Issue tracking is an automated workflow that notifies you and gives a holistic view of packages that require your attention.
Together with a detailed activity log, Bytesafe helps by tracking all updates and changes to package versions making it easy to follow what actions have been made when and by who.

In addition, package quarantine allows for automatic block of packages that surpass security threshold levels, for example critical vulnerabilities like Spring4shell. Providing time for your organization to decide the best path forward according to your needs.
Software composition analysis of Git repositories
Source composition analysis allows users to link their Git repositories to Bytesafe for continuous dependency analysis. Bytesafe detects components directly from repositories and uses existing project files to identify direct and transitive dependencies - providing an overview of dependencies in mere seconds.
Initial support for JavaScript and Go modules, with support for gradle projects and NuGet lock files, lockfile linting and detection of configuration issues in the roadmap.
Want to improve your Java supply chain security?
Bytesafe provides secure Maven registries for all your organization’s Java package dependencies. Automatically track all your dependencies and get notified about issues such as known vulnerabilities.
The Dependency Firewall provides end-to-end security to protect your supply chain before harm is done. Unlike traditional security software Bytesafe acts where others report after the fact. Keep insecure open source dependencies away from your developers, CI/CD and applications. Enforce business rules and ensure secure and compliant dependencies for the whole organization!
Want to know more? Book a demo or Sign up for Bytesafe and get started today for free!





