
Open source software adoption reaches higher levels every year. Recent figures show that over 70% of code used in codebases is open source. With a constant stream of new components comes increased requirements to manage the inherent risks associated with open source. Requirements that quickly turn into a necessity as supply chain attacks increased by 400% in 2021.
The practice to identify and track open source components usually falls under the umbrella of Software Composition Analysis (SCA). Using SCA, teams can manage known security vulnerabilities, prevent dependency threats and consider open source license compliance needs for the packages they depend on. All natural parts of Bytesafe.
And with our latest addition: Software Composition Analysis directly from Git source repositories it’s easier than ever to manage open source risk in Bytesafe, with:
- Source repository analysis: Scan Git repositories and make sure declared dependencies are as safe as the rest of your software supply chain.
- Package registries & Dependency Firewall: Secure package management with knowledge and control over the packages used by your developers and CI/CD.
Get started and add your Git source repositories to Bytesafe! No need for new tools or forced procedures. Approachable supply chain security, a win for everyone!
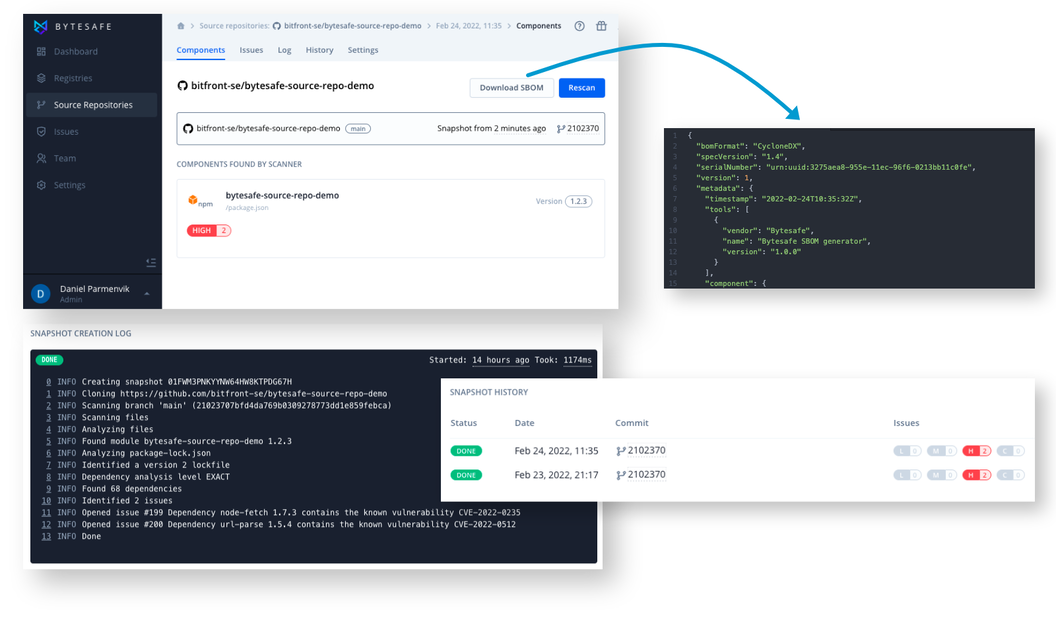
What is Software Composition Analysis (SCA)?
Software Composition Analysis (SCA) is a method to keep track of the open source components used in a specific application or for a whole software supply chain.
The output from SCA tools is typically a list of components (direct and transitive dependencies) and any associated vulnerabilities, open source licenses or other configuration issues. Standardized this is usually referred to as a Software Bill of Materials (SBOM).
Shift left: Scan repositories after each Git commit
Most projects use open source packages available from public registries. The direct dependencies (the ones developers include directly in the project) are listed in project files like package.json (Npm), pom.xml (Maven), go.sum (GoLang) or .csproj (NuGet). But the total number of dependencies are often much larger than those listed in the project files as dependencies have dependencies of their own.
Staying in control of all these packages used in the software supply chain can be a real challenge without the right tools. Traditionally this responsibility has been left to the developers and tracking of software composition made a part of the build process.
However it’s easier and cheaper to remediate issues earlier in the SDLC. And if your SCA scanning is linked to builds, how do you track applications that are rarely, if ever built?
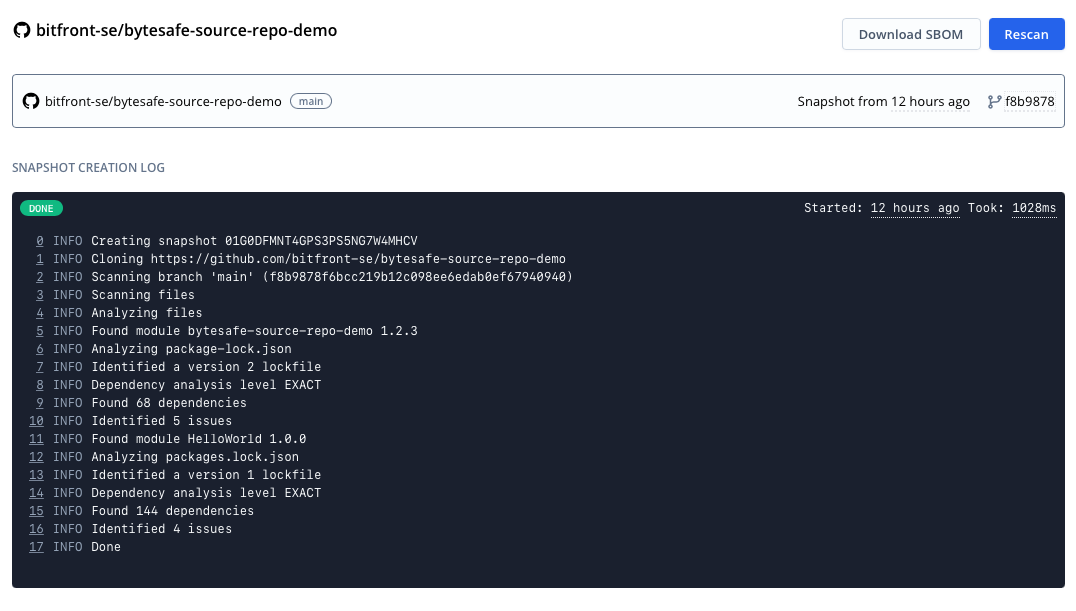
Good SCA tools identify issues early and make it easy to track every application - new or old. Shift left with Bytesafe and identify issues from every commit to the code repository - and continuously monitor your existing software composition for new issues.
Let’s review some benefits of using Source Repositories in Bytesafe to keep track of your software composition.
Scan any Git repository
Bytesafe can scan any Git repository, private or public and you are not limited to repositories in GitHub or from a single provider.
If your team uses GitHub for newer applications and code for older legacy applications are held in a local Git branch setup, you can easily add both these sources. Making sure you avoid blindspots and miss important issues.
Automatically scanned when needed
Source repositories are continuously scanned - every 24 hours or automatically when changes are detected in project files. In a world with a constant stream of new vulnerabilities and advisories it’s imperative not only to track changes and new dependencies, but also track issues for existing applications and dependencies.
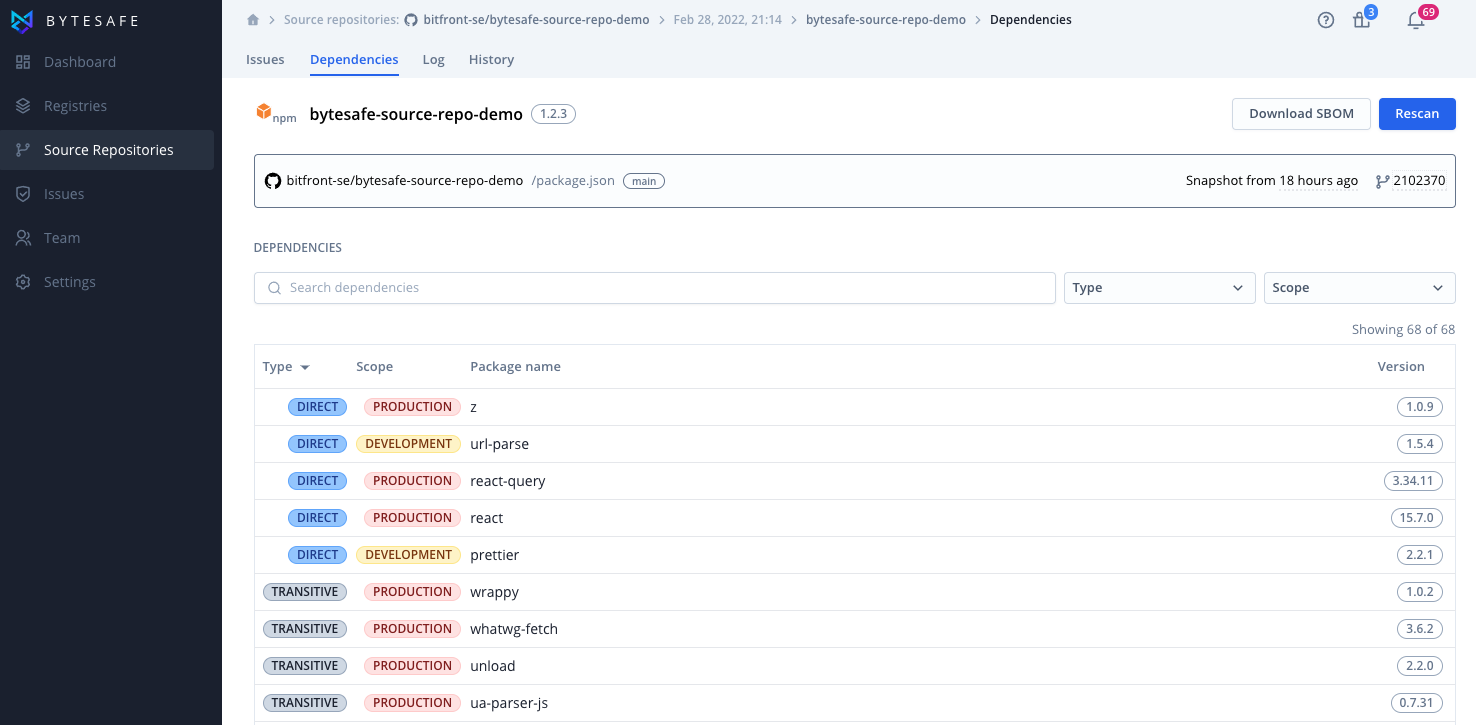
Multiple ecosystems and modules in one place
Bytesafe identifies components for several ecosystems from a single repository. If your project uses Go modules for backend and JavaScript for frontend, Bytesafe will identify those different components and list their dependencies.
Do you have many different projects spanning multiple ecosystems? No problem, simply add the source repositories and Bytesafe will do the rest for you.
Bytesafe also identifies components from all the major JavaScript package managers, npm, yarn and pnpm so you can track projects using alternate lock files like yarn.lock and pnpm-lock.yaml.
Linting lock files to identify configuration issues
Identifying security issues is only part of the equation. There are many other just as critical configuration and linting issues users need to remediate to keep a supply chain secure.
Scanning lock files in code repositories grants unique opportunities to identify configuration issues and enforce that they use secured packages from Bytesafe. Here is an excerpt of planned additions to the Source Repository Scanner already on the roadmap:
- Identify Git dependencies. Many package managers allow dependencies to be fetched directly from remote Git repositories. A solution intended for flexibility, but one that also opens critical security holes where dependencies can completely bypass security infrastructure. A possible attack vector for malicious packages to enter the supply chain.
# Example of a supply chain configuration issue. A dependency resolving directly to a Git repository, skipping the intended supply chain
"node_modules/js-function-reflector": {
"version": "1.3.0",
"resolved": "git+ssh://git@github.com/leonardiwagner/js-function-reflector.git#f3a1295909cf870bbb7bb136ca53796fc3e87c17",
"license": "MIT"
},
...
- Identify dependencies resolved from multiple sources. Multiple sources in lock files indicate a potential configuration error where a faulty lock file has been committed to the repository. This also includes enforcing use of secured packages from Bytesafe registries.
What about SCA scanning with CLI tools?
Successful supply chain security is complex and we want to facilitate for users to protect their supply chain from multiple angles. That’s why our roadmap includes CLI support for Bytesafe’s SCA capabilities.
With the Bytesafe CLI users can then verify and scan installed packages directly in build environments. A necessity for higher levels of accuracy in ecosystems that do not support lock files.
Getting started with Source Repositories in Bytesafe
The Source Repository Scanner detects JavaScript, Go and NuGet components directly in your Git repositories (with support for gradle projects soon to come). The scanner uses existing lock files and project files to identify both direct and transitive dependencies.
Source repositories are added using either the URL of a Git repository, or a selected repository directly from a list of linked GitHub repositories when using the GitHub integration in Bytesafe.
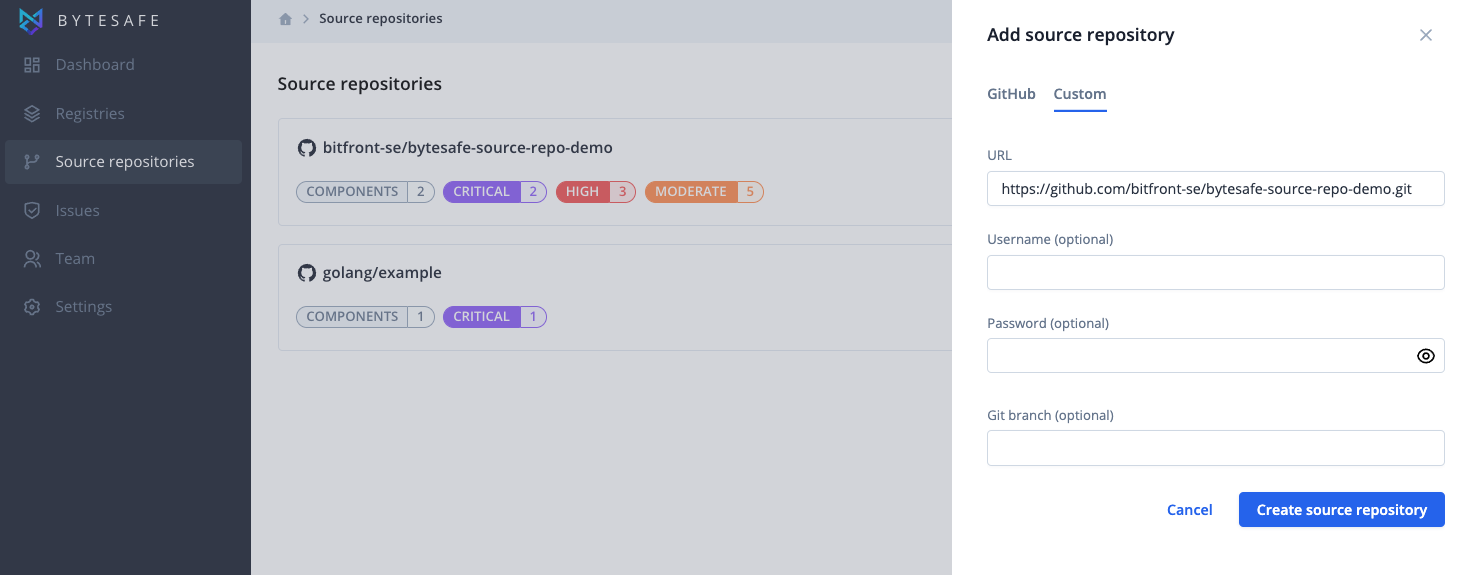
To scan a specific Git branch, users can easily provide which one to use. If none is provided the default branch will be selected.
After a source repository has been added, the initial scan is initiated directly. After that, each repository is scanned every 24 hours or automatically when code changes are detected when using the GitHub integration.
Rescan automation and integration directly with GitHub
When a new commit alters the package dependencies in a linked Git repository you want to be notified of any issue directly. Fortunately the GitHub integration triggers automatic rescans of your repositories whenever changes are detected in project files.
Source repository analysis in Bytesafe can be added for any linked GitHub repository. Add the GitHub Integration to your workspace to get started.
Downloading SBOMs
SBOMs in Bytesafe are JSON files in a CycloneDX format. Download and share SBOMs either for whole repositories or for individual components.
# Example: SBOM JSON file from Bytesafe
{
"bomFormat": "CycloneDX",
"specVersion": "1.4",
"serialNumber": "urn:uuid:ceafb7f8-996e-11ec-96f6-0213bb11c0fe",
"version": 1,
"metadata": {
"timestamp": "2022-02-28T20:14:17Z",
"tools": [
{
"vendor": "Bytesafe",
"name": "Bytesafe SBOM generator",
"version": "1.0.0"
}
],
"component": {
"bom-ref": "pkg:npm/bitfront-se/bytesafe-source-repo-demo@1.2.3?repository_url=https:/github.com/bitfront-se/bytesafe-source-repo-demo",
"type": "library",
"name": "bytesafe-source-repo-demo",
"version": "1.2.3",
"purl": "pkg:npm/bitfront-se/bytesafe-source-repo-demo@1.2.3?repository_url=https:/github.com/bitfront-se/bytesafe-source-repo-demo"
}
},
"components": [
...
Want to improve your supply chain security?
In addition to Software Composition Analysis, Bytesafe provides secure Npm, NuGet and Maven registries for all your organization’s package dependencies. Combined with the Dependency Firewall Bytesafe provides end-to-end security to protect your supply chain before harm is done.
Want to know more? Book a demo or Sign up for Bytesafe and get started today for free!





