The Bytesafe Solution
Protect your Java supply chain

Fully Managed Repositories
Private artifact repositories for both Maven and Gradle projects

Software Composition Analysis
Identify open source dependencies in your applications
Dependency Firewall
Automatically block vulnerable components for a secure maven supply chain

Vulnerability & License Scanning
Continuously scan and monitor your dependencies. Get notified of any issues

Issue tracking & Remediation
Identify issues & take action. Keep track every step of the way
Firewall for Java dependencies
Discover bytesafe
Secure Maven artifact repositories
Manage your Java dependencies with Bytesafe
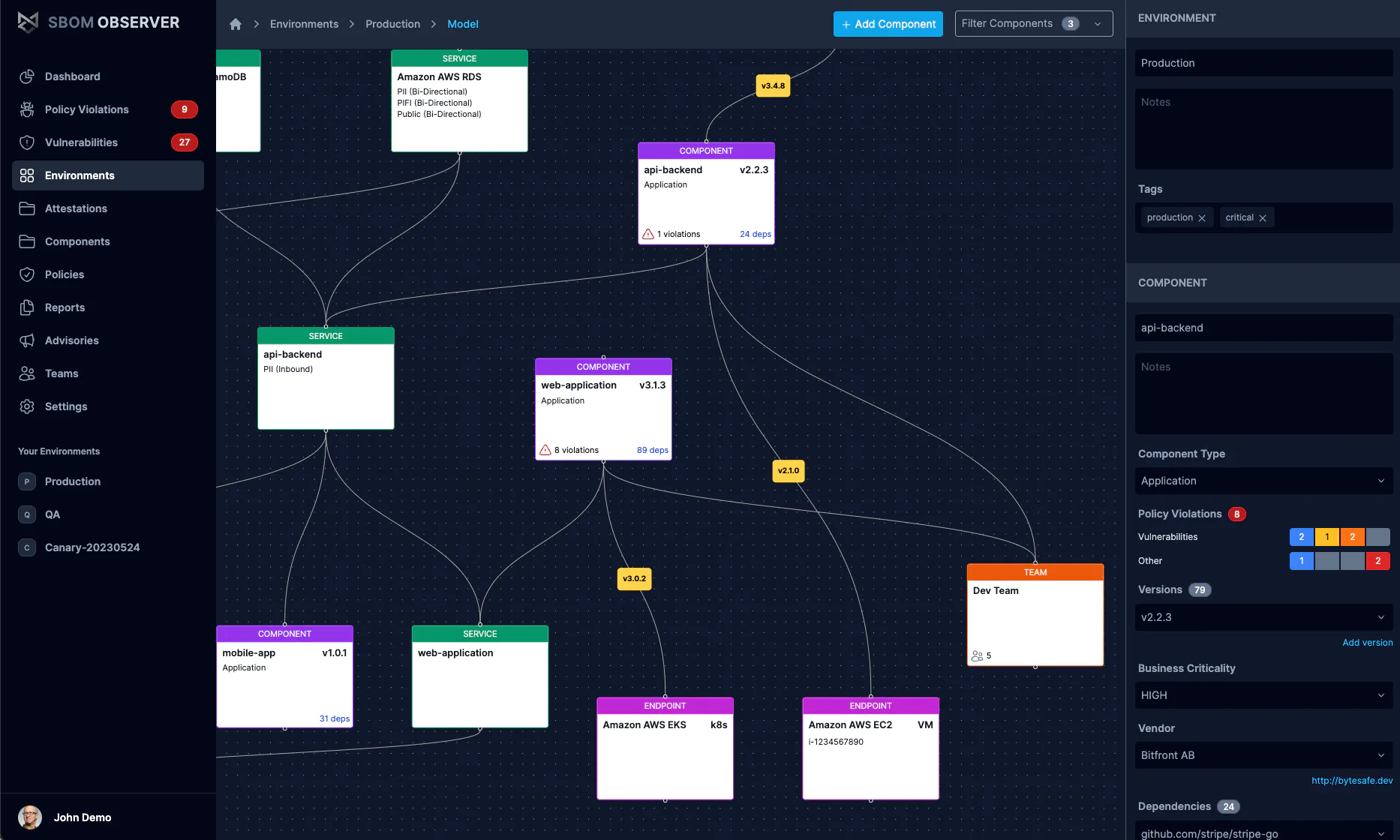
Control the Maven artifacts used across your organization for Java, Kotlin, Scala and other JVM languages. Add both private and public artifacts to your secure single source.
Get insight into what artifacts are used and the issues require your attention. Explore detailed information about your packages in an intuitive user interface.
Secure source for developers and CI/CD
Protect your supply chain with secure and compliant Java dependencies for your developers and CI/CD systems.
Secure access to a single source of truth for Maven artifacts for the whole organization.
Block unwanted packages
Don’t risk a security breach! Block undesirable packages from getting into your software supply chain.
Continuously monitor dependencies for potential threats, get notified and enforce business policies at every action you make.
Share. Cache. Proxy. Collaborate
Unlock productivity by configuring your team’s source of truth for Maven and Gradle projects. Cache/proxy artifacts from public repositories like Maven Central and deploy the private artifacts your organization needs.
Fully managed and hosted in the cloud. High availability and quality results, all the time!
Continuous License Compliance
Track risk. Enforce policy. Prove compliance.
Go beyond SBOM generation with SBOM Observer— a platform built for SBOM-centric workflows from ingestion to reporting.
Enforce policies automatically, monitor vendor and internal risk in one view, and produce regulator-ready proof on demand for customers and auditors alike.
By Developers for Developers
Work using your regular tools
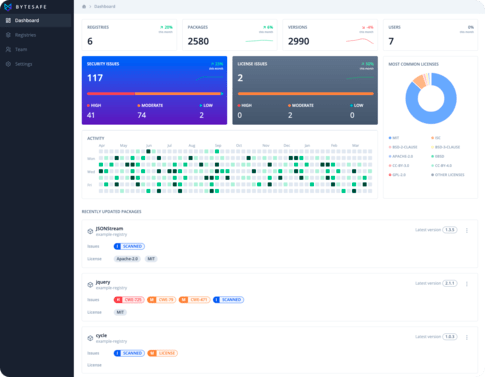


Build Maven compatible projects using your regular tools like mvn and gradle. Create secure access tokens, configure use of the repository and install/deploy packages. Setup your project to use Bytesafe for internal and public Maven dependencies and benefit from the added value from the Bytesafe platform.
Integrations
Bytesafe integrates with the services you use